MANAGED HOLISTIC
Zero Trust Complete
Covering all parts of cybersecurity to ensure better security and full compliance
MANAGED HOLISTIC
Zero Trust Ecosystem
Covering all parts of cybersecurity to ensure better security and full compliance
Verify First, Then Trust
For Your Firm Security & Compliance
Endpoint
Security
Automating and managing the enforcement of cyber settings and advanced endpoint protection
User
Security
Verifying that only authorized users can access data, endpoints, software, and networks
Network Security
Enforcing secure and encrypted communication inside and outside corporate networks
Cloud App Security
Hardening software and validating the compliance of users, and networks at the time of login
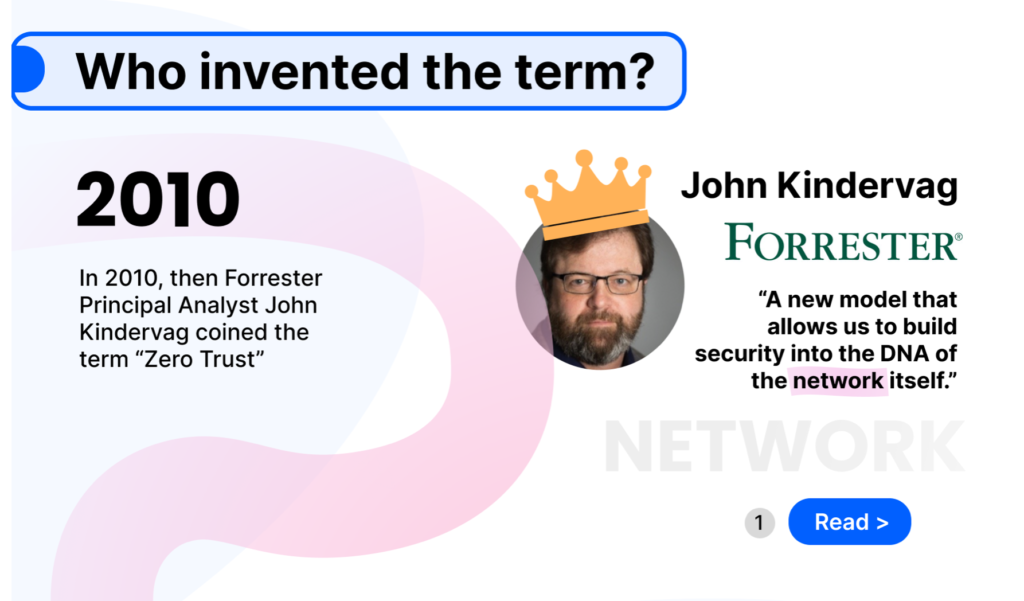
PREPARATION
Identity & Access Management
A framework of policies and technologies to ensure the right users and devices have the appropriate access to right systems and technology resources
Cybersecurity Ecosystem Strategies
- Zero Trust strategies and considerations
- Identity governance and administration
- Privileged access management
Zero Trust Delivered!
Validation of Compliance at the Time of Login
To stop unknown users, unknown devices, from unknown networks, from accessing systems of private data
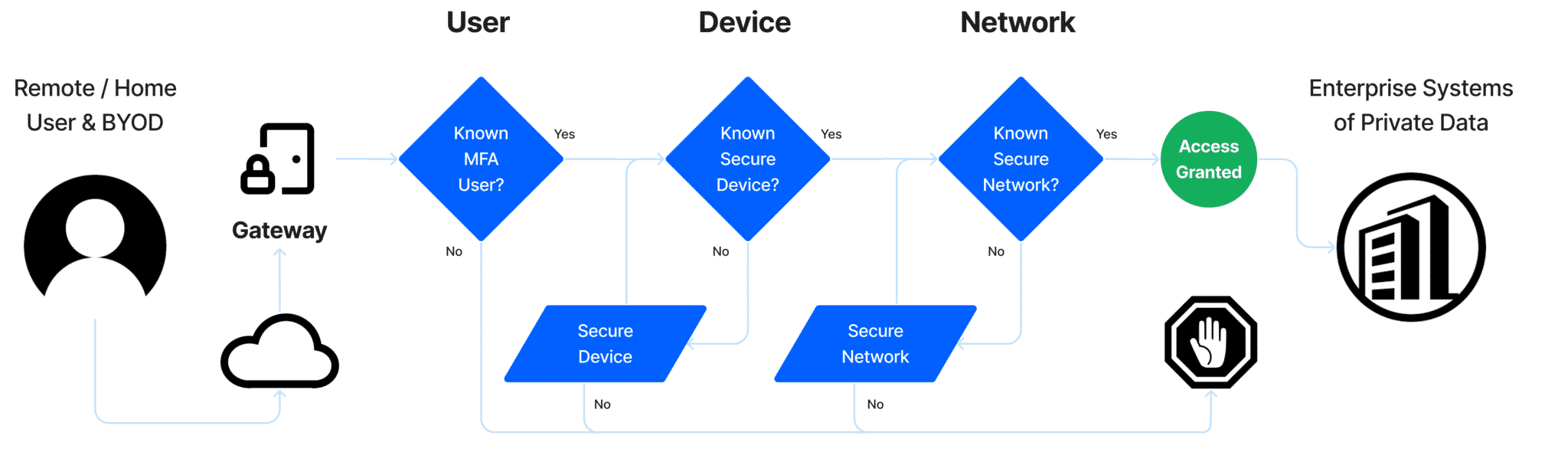
ZERO TRUST
Web App Security Gateway
Systems of Private Data Gateway
Protection against unauthorized users and non-compliant endpoints
One of your biggest risks is having users login to a system of private data with unknown devices. FCI’s solution validates the cyber posture of a device before allowing it to access the system.
Integration with Web App Identification Gateway
- Automated deployment of cybersecurity software agents
- Evidencing compliance of technical controls at the time of access to Systems of Private Data
Device Identification
- Blocking unknown devices from accessing private data
- Matching usernames and devices
Enforcement
- Enforcing all devices (BYOD and firm-owned) connected to Workgroup, Domain, Azure, Live, or iCloud
- Evidencing compliance of technical controls with Asset Inventory Report and Dashboards
- Mass Vulnerability Response