UNIQUE MODEL
Co-Managed Cybersecurity Services
FCI partners with Enterprises, their internal IT teams, and MSPs to define custom cybersecurity solutions that augment and adapt to teams' skill sets while leveraging existing systems, processes, and practices.
New Reality Calls for New Models
This is a call for all-hands-on-deck to rally together and optimize complementary expertise
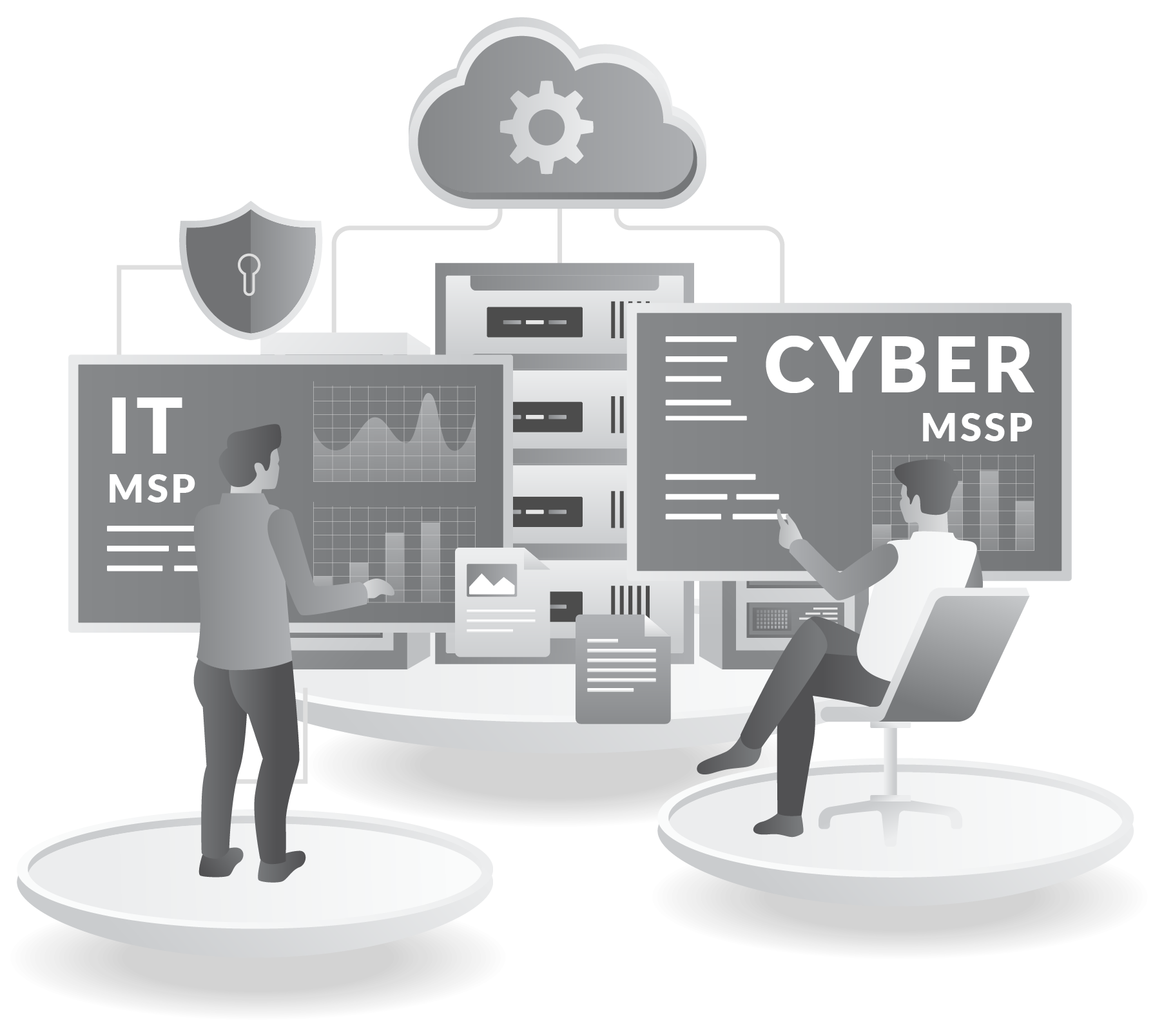
Co-Managed Cybersecurity Model
Benefits
Reduced Cybersecurity Risks
Stronger Checks & Balances
Greater Visibility into Ecosystem

Security and Risk Management Spending to Exceed $150 Billion in 2021
Cybersecurity is now the #1 IT spend
INNOVATION
Holistic Zero Trust Ecosystem
FCI proposes an innovative Co-Managed Cybersecurity model for larger firms in cyber-regulated industries to better fit in their current complex environments, fill gaps in their systems and expertise, as well as ensure ultimate Zero-Trust security in all areas.
Design a Custom Zero Trust Ecosystem
- Select and integrate cybersecurity solutions
- Ensure Zero-Trust for users, endpoints, networks, and systems of private data
Protect Past Investments
- Leverage existing systems and build around them
- Adapt to and enhance established policies and procedures
Establish Clear Roles & Responsibilities
- Leverage teams' experience and expertise
Harden Web Apps & Cloud Environments
- Revise and improve cybersecurity configurations and settings
- Evidence hardening for better compliance
- Facilitate vendor risk management
The SOAR platform we built to deliver our services
Integration and hardening of best-of-breed software in a private, redundant infrastructure
While IT teams and MSPs are managing critical systems, networks, users, and more, cybersecurity continues to grow as a category in scope, function and type. Ransomware has been a hot topic as attacks increase and the threat landscape is an ongoing challenge.
FCI’s team of seasoned cybersecurity experts, combined with an integrated technology built for cyber-regulated industries, gives organizations of all types and sizes a way to secure environments with a zero-trust approach using a framework and technologies to ensure proactive protection and compliance.


