FCI SOAR
Platform
An integrated, modernized cybersecurity platform built for compliance alignment from years of experience in cyber-regulated industries with the modules needed to effectively service companies of all types and all sizes
Security Automation

Security Automation for Scalability
Cyber consistency cannot be achieved through a manual process
MANAGED
Endpoint & Network Protection
“Managed” means you have nothing to do. Without user disruption or interruption, FCI protects your endpoints and networks while you focus on your core business.
Thanks to tamper protection, no program or individual can disable, uninstall or change what we manage. This ensures your cyber settings and tools adhere to your policies and procedures.
Compliance Requirements
- According to the Written Information Security Policy (WISP) from your firm
- Enforce the specific cybersecurity regulations applicable to your firm
- Protect your data, your users and your firm
- Automated enforcement of security settings and tools
- Protect networks with managed firewall services
- Work securely from anywhere with Gateway VPN

Office, BYOD, Home, Remote, Travel... and Space!
CYBER POSTURE
Evidence of Compliance
Attestations are no longer enough. In the event of an audit, an exam, or a breach, you will have to demonstrate evidence (proof) that you are compliant. No worry, we have you covered.
The best way to prepare for this, and a cybersecurity regulation requirement, is to let us perform a Technical Controls Scanning & Evidencing of your systems, devices, and networks.
NIST-Based Asset Inventory Report
- Inventory of endpoints and their cyber posture
- Enables faster responses to security alerts by revealing device information
- Automatically sent over public network (time stamp)
SIEM for Persistent Audit Trails
- Log aggregation from systems provided by FCI managed services
- Log retention at FCI Data Centers
- On-demand reporting during incident or breach
Safeguards Scanning & Evidencing
- Corporate Internet Attack Surface Assessment (CIASA)
- Network penetration testing
- Vulnerability scans
- Evidence compliance of environment and systems
- Recommendations and report
MANAGED HOLISTIC
Zero Trust Ecosystem
Covering all parts of cybersecurity to ensure better security and full compliance
Verify First, Then Trust
A Zero Trust approach considers users, endpoints, software, and networks as potential threats until proven otherwise
Users
Verifying that only authorized users can access private data, endpoints, software, and networks
- Identity Management
- Password Management
- Single Sign-On
- Multi-Factor Authentication
Endpoints
Automating and managing the enforcement of cybersecurity settings and endpoint protection
- Cyber Settings
- Full-Disk Encryption
- Antivirus, Anti-Malware & Ransomware
- Endpoint Detection & Response
Software
Hardening software and validating user and endpoint compliance at the time of login to systems or private data
- Vendor Risk Management
- Software Hardening
- Restricted Websites and Software
- Data Exfiltration Protection
- Web App Security Gateway
Networks
Enforcing secure and encrypted communication inside and outside corporate networks
- Firewall Hardening
- Secure Remote Communication
Zero Trust Delivered!
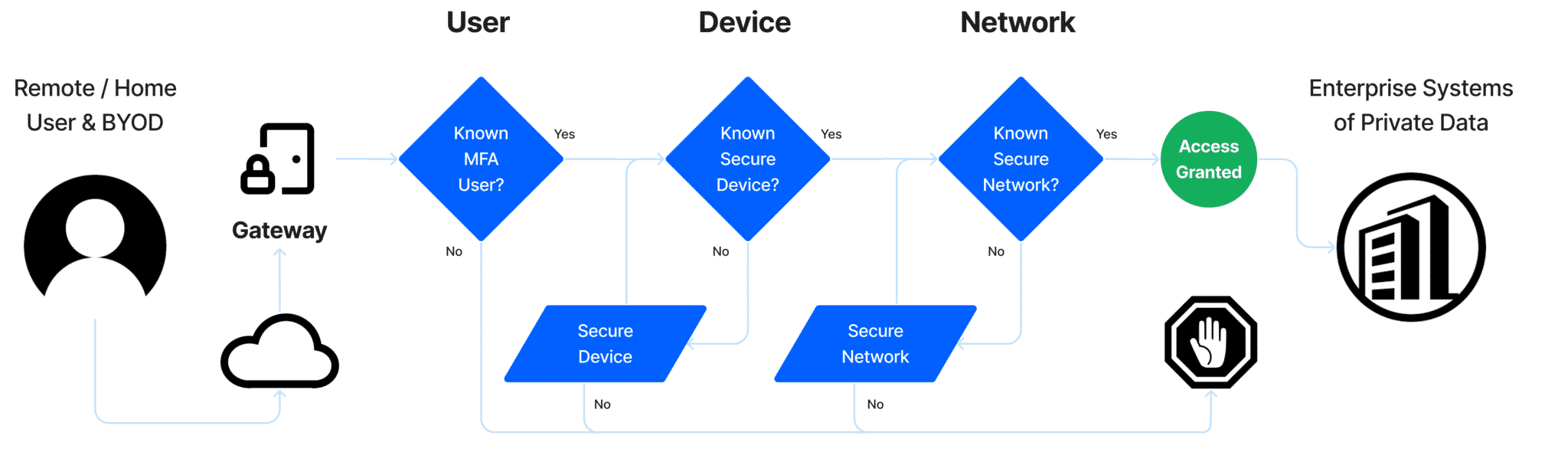
Validation of Compliance at the Time of Login
To stop unknown users, unknown devices, from unknown networks, from accessing systems of private data
ZERO TRUST
Web App Security Gateway
Systems of Private Data Gateway
Protection against unauthorized users and non-compliant endpoints
One of your biggest risks is having users login to a system of private data with unknown devices. FCI’s solution validates the cyber posture of a device before allowing it to access the system.
Integration with Web App Identification Gateway
- Automated deployment of cybersecurity software agents
- Evidencing compliance of technical controls at the time of access to Systems of Private Data
Device Identification
- Blocking unknown devices from accessing private data
- Matching usernames and devices
Enforcement
- Enforcing all devices (BYOD and firm-owned) connected to Workgroup, Domain, Azure, Live, or iCloud
- Evidencing compliance of technical controls with Asset Inventory Report and Dashboards
- Mass Vulnerability Response

Cybersecurity Examination Initiative
SEC Risk Alert Volume IV, Issue 8
"... monitoring exfiltration and unauthorized distribution of sensitive information outside of the Firm through various distribution channels (e.g., email, physical media, hard copy, or web-based file transfer programs) and any documentation evidencing this monitoring."
Protection Against Data Exfiltration
Advanced solutions for Home Offices and Enterprises
ZERO EXFILTRATION
Cybersecurity Policy Violation System
Data Exfiltration Protection
Data Leakage Protection (DLP)
Management Tools
- Alerts, reports, and dashboards
Web Controls
- Monitoring and blocking restricted Websites
- Third party Web apps allowed and not allowed
- Monitoring for unknows Web apps
Removable Storage (USB, Drive, etc.)
- Monitoring and blocking removable storage, local and Web storage apps
File Content
- Monitoring and blocking file content from being exfiltrated


