IDENTIFY
Evidence of Compliance
The first domain of NIST is to identify your assets and your risks
CYBER POSTURE
Evidence of Compliance
Attestations are no longer enough. In the event of an audit, an exam, or a breach, you have to demonstrate evidence (proof) that you are compliant. No worry, we have you covered.
The best way to prepare for this, and a cybersecurity regulatory requirement, is to let us perform Safeguard Scanning & Evidencing of your cloud, systems, devices, and networks.
NIST-Based Asset Inventory Report
- Inventory of endpoints and their cyber posture
- Enables faster responses to security alerts by revealing device information
- Automatically sent over public network (time stamp)
SIEM for Persistent Audit Trails
- Log aggregation from systems provided by FCI managed services
- Log retention at FCI Data Centers
- On-demand reporting during incident or breach
Safeguard Scanning & Evidencing
- Corporate Internet Attack Surface Assessment (CIASA)
- Network penetration testing
- Vulnerability scans
- Evidence compliance of environment and systems
- Recommendations and reports
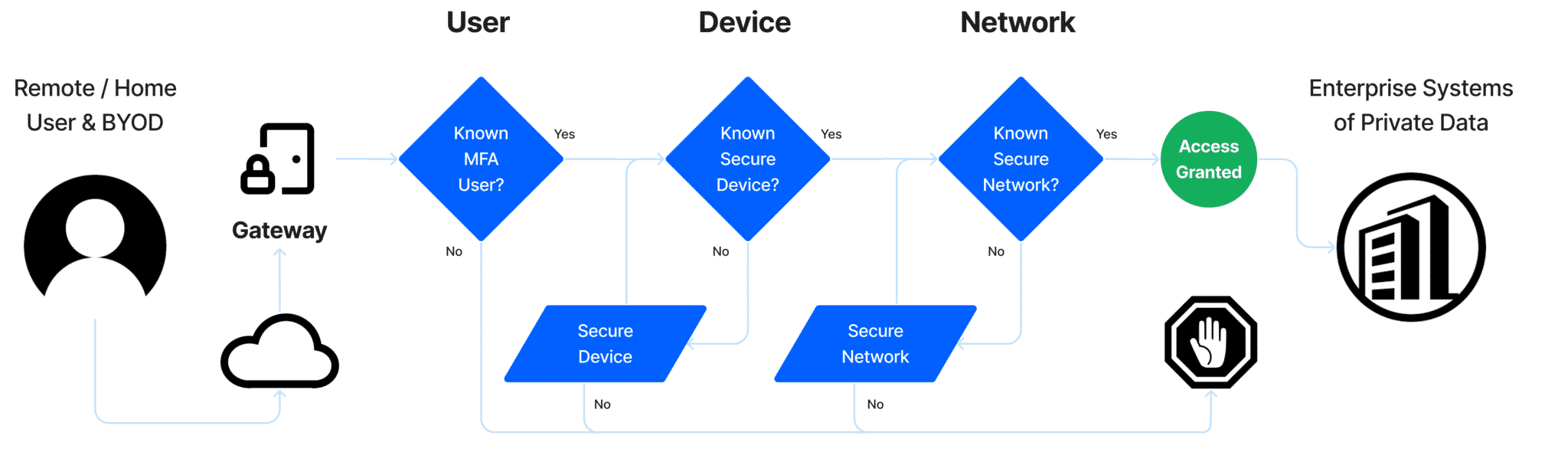
ZERO TRUST
Cybersecurity Policy Enforcement System
Systems of Private Data Gateway
Protection Against Unknown & Unsecure Devices
One of your biggest risks is having users login to a system of private data with unknown devices. FCI’s solution validates the cyber posture of a device before letting it access the system.
Integration with Web App Identification Gateway
- Automated deployment of cybersecurity software agents
- Evidencing compliance of technical controls at the time of access to Systems of Private Data
Device Identification
- Blocking unknown devices from accessing private data
- Matching usernames and devices
Enforcement
- Enforcing all devices (BYOD and firm-owned) connected to Workgroup, Domain, Azure, Live, or iCloud
- Evidencing compliance of technical controls with Asset Inventory Report and Dashboards
- Mass vulnerability Response
Zero Trust Delivered!
Validation of Compliance at the Time of Login
To stop unknown users, unknown devices, from unknown networks, from accessing systems of private data