Introduction
This paper outlines how the NIST Framework (National Institute of Standards and Technology) is being used in the Financial Services Industry to provide structure and consistency to Cybersecurity. With the increasing volume of cyber-attacks, the Financial Services Industry is finding ways to efficiently approach Cybersecurity risk. “The reality is, Financial Services firms are reportedly hit by security incidents a staggering 300 times more frequently than businesses in other industries.” (1)
Cybersecurity, sometimes called Information Technology Security, focuses on safeguarding endpoints, networks, programs and data from unlicensed or spontaneous access. The growth of cyber incidents has spurred the growth of cybersecurity solutions, many of which are cloud-based. Cybersecurity protection has become such a concern that large Enterprises, Insurance Companies and Broker-Dealers now have internal cyber teams with Chief Information Security Officers (CISOs), cyber experts and technicians. “CISOs at Financial Services institutions reported that up to 40% of their time was spent on compliance requirements of various regulatory frameworks, not cybersecurity.” (2)
Cybersecurity is Now a Major Segment of Information Technology
As the dynamic Cybersecurity segment grows, it has become an industry unto its own. Similar to how SEO and Digital Marketing grew in the Marketing segment with rapid technology advancements, online business growth and new vendors created just for this function, there are now a range of compliance firms and Managed Security Service Providers (MSSPs) specializing in only Cybersecurity technologies and services.
Key drivers for growth are regulatory and compliance demands, growth in IoT and the rise in malware and phishing threats. Additionally, large enterprises have internal cyber teams but are looking for cyber solutions for their decentralized independent sales offices (branches and agencies) with BYOD models. Both large and small firms are often partnering/outsourcing this function to manage the components, layers, regulations and controls for better reporting and evidence of compliance. In many cases, with how quickly the cyber environment changes, it has become too complex and costly to manage in-house.
“Ponemon Institute’s 2018 Cost of Data Breach Study reports the global average cost of a data breach is up 6.4 percent over the previous year to $3.86 million. The average cost for each lost or stolen record containing sensitive and confidential information also increased by 4.8 percent year over year to $148.”
2018 13th Annual “Cost of a Data Breach Study” by IBM / independently conducted by Ponemon Institute (3)
A range of vendors have emerged to meet this demanding market since the Financial Services Industry is one of largest cyber targets due to high sensitivity of public and non-public data.
When a breach occurs, a firm’s readiness is put to the test. Reputation, financial loss and legal repercussions may become a financial drain and a fire to put out. The goal is to shift attention towards prevention while having a full structure for incident identification and response. Putting the right cyber framework and tools in place with the right controls and automation (limiting human involvement) have a powerful impact in adhering to regulatory compliance while reducing the human error factor. (4)
1. Statistics on Financial Services Cybersecurity Compliance
- A SEC Cybersecurity sweep examination by the SEC’s Office of Compliance Inspections and Examinations (OCIE) found that 88 % of Broker-Dealers (BDs) and 74 % of the Registered Investment Advisors (RIAs) they visited experienced cyber-attacks directly or indirectly through vendors.
- The sweep found that while the vast majority of all BDs and RIAs have adopted Written Information Security Policies, the SEC staff found some gaps in Cybersecurity protection among many firms.
- Moreover, OCIE reports that more than half of the BDs, and almost half of the RIAs they examined reported receiving fraudulent emails seeking to transfer client funds. Over a quarter of the BDs reported losses related to fraudulent emails, but no single loss in excess of $75,000. (5) (6)
1.1 There are Still Gaps in Cybersecurity Enforcement
From Written Information Security Policies (WISPs) to Continuity Plans and Periodic Risk Assessments, firms are trying to put tools and standards in place to comply with regulations. This said, many still do not have:
- Cyber teams in place
- Ability to report and prove full compliance
- 3rd-Party Vendor Cybersecurity requirements put into contracts and procedures in place related to information security training for employees, vendors and business partners
- Very few firms still address how they determine whether they are responsible for client losses resulting from cyber incidents
- Even fewer have Cybersecurity insurance or a CISO in place
1.2 3rd SEC Cybersecurity Sweep Announced
The Securities and Exchange Commission’s (SEC’s) Office of Compliance Inspections and Examinations (OCIE) has launched a third Cybersecurity sweep, announced by deputy director Kristin Snyder, on March 19th at the Investment Company Institute’s 2019 Mutual Funds and Investment Management Conference in San Diego, California. The third Cybersecurity sweep will focus primarily on Cybersecurity practices at investment advisers, encompassing firms with multiple branch offices and those involved in recent merger and acquisitions (M&As). (7)
This leads to why standards and a framework are so important for the Financial Services Industry
2. History and Creation of the NIST Framework
The NIST Framework for Improving Critical Infrastructure Cybersecurity (“The Framework”) is an Executive Order 13636 that was signed by President Obama on February 12, 2013. The Executive Order introduced efforts on the sharing of Cybersecurity threat information, and on building a set of current and successful approaches, a framework, for reducing risks to critical infrastructure. Through this Executive Order, NIST was tasked with the development of a “Cybersecurity Framework.”
2.1 Why NIST?
NIST was selected for the task of developing the Framework because they are a non-regulatory federal agency that acts as an unbiased source of scientific data and practices, including Cybersecurity practices. NIST’s mission is to promote U.S. innovation and industrial competitiveness. NIST has a long history of successfully addressing critical national issues through partnerships with industry, academia, and other government agencies. This kind of collaboration would be critical for the Framework to be successful. The Framework was, and continues to be, developed and promoted through ongoing engagement with, and input from, stakeholders in government, industry, and academia. (8)
2.2 Standard NIST Framework
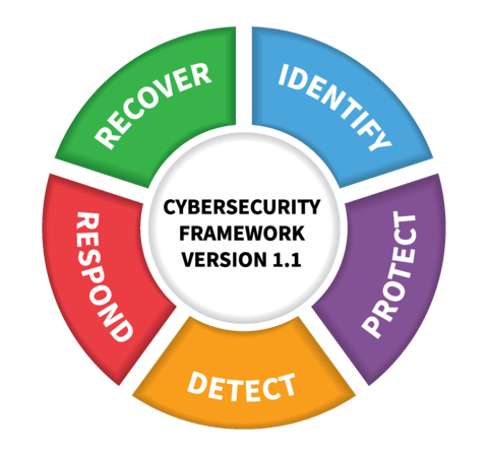
3. How the NIST Framework Applies to the Financial Services Industry & Benefits
3.1 Ongoing Support of the NIST Framework
U.S. Financial Services industry has been consolidating around the NIST Cybersecurity Framework as its go-to-approach for cyber risk management and streamlining compliance, with a focus on third-party risk. For years, leading Financial institutions have highlighted the NIST Framework’s superior approach in protecting Financial and economic platforms.
The Framework is recognized for providing an enhanced understanding of the state of Cybersecurity for regulators and industry, reducing administrative burdens and regulatory compliance complexity, and offering more efficient and effective resource allocation to address risk. A more vital aspect of the NIST Framework is its capacity to maximize Cybersecurity and compliance in complement with various industry-specific extensions, as evidenced by the Financial Services Sector Cybersecurity Profile.
3.2 Financial Services Sector Cybersecurity Profile
On October 25, 2018 at an event at the National Press Club, the Financial Services Sector Coordinating Council (FSSCC) along with a group of leading Financial trade associations unveiled the sector’s Cybersecurity Profile, an initiative that NIST has called “…one of the more detailed Cybersecurity Framework-based, sector regulatory harmonization approaches to-date.” In addition to releasing a statement of support with the publication of the Profile, NIST has been an active facilitator and partner in its development.
The Profile is a Financial Services sector-specific extension of the NIST Framework developed to better address the sector’s Cybersecurity environment, protection needs, and regulatory requirements. Specifically, the Profile seeks to provide Financial Institutions and their third-party providers with more consistent and efficient processing of examination material by firms and regulators. It also helps regulators and firms to prioritize resources and focus on cyber threats of greatest concern.
As the Profile Evolved, its Design became Rooted in the NIST Cybersecurity Framework’s Five Functions, Categories, and Subcategories
The Financial Services Sector Cybersecurity Profile (or FSP) is a Framework based on:
- Complimenting the NIST Cybersecurity framework
- Integrating widely used standards and supervisory expectations
- Bringing plain language to benchmarking, risk management, audit, and in-house education
- Offering compliance efficiencies that grow with a Financial institution’s complexity
- Aiding prioritization and focused use of resources
- Enhancing internal and external oversight, due diligence and risk identification using consistent terms and concepts
- More efficient third-party vendor management review and oversight
The Profile is designed for all Financial institutions, Financial Services companies, Financial firms, and their third-party providers. A broad cross-section of the Financial Services industry – banking, insurance, asset management, market utilities, Broker-Dealers – designed the Profile to scale across institutions of varying complexity, interconnectedness, and criticality. (9) (10) (11)
4. Top 5 Ways the Financial Services Industry Can Leverage the NIST Framework for Cybersecurity Compliance
4.1 Take Advantage of Industry Partnerships and Resource References
Reference 1: SEC & FINRA
Both the U.S. Securities and Exchange Commission (SEC) and Financial Industry Regulatory Authority (FINRA) have issued guidance to Broker-Dealers on Cybersecurity, providing valuable resources for them and for Registered Investment Advisors to combat the growing threat of cyber-attacks. These reports should provide the tools and information needed by those Broker-Dealers who have put off focusing on Cybersecurity to strengthen their data protection capabilities. (12)
- SEC’s Office of Compliance Inspections and Examinations (OCIE) Cybersecurity Sweep Examinations (13)
- Financial Industry Regulatory Authority (FINRA)’s Rules and Guidance (14)
Reference 2: NIST and FSSCC Team Up for Financial Services Cybersecurity
The Financial Services Sector Coordinating Council (FSSCC) held a workshop hosted by NIST in Washington, D.C. in 2018, to further develop the Financial Services Profile of the framework. It gathered not only industry members but also regulators such as the FED and the OCC. (15)
Reference 3: Federal Financial Institutions Examination Council (FFIEC) Cybersecurity Assessment Tool
In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council (FFIEC) developed the Cybersecurity Assessment Tool (Assessment) to help institutions identify their risks and determine their Cybersecurity preparedness. (16)
4.2 Core Traits of Adaptive Companies Reaching High Levels of Level Maturity
Over the past two years (2017-2018), Deloitte has worked with the Financial Services Information Sharing and Analysis Center (FS-ISAC) to survey members on how they are confronting cyber challenges.
They identified several core traits of companies that have already reached the highest maturity level as defined by the National Institute of Standards and Technology (NIST).
These defining characteristics of “adaptive” companies, which are alluded to in the NIST Cybersecurity maturity framework, include:
- Securing the involvement of senior leadership, both top executives and the board;
- Raising Cybersecurity’s profile within the organization beyond the information technology (IT) department to give the security function higher-level attention and greater clout; and
- Aligning Cybersecurity efforts more closely with the company’s business strategy. (17) (18)
4.3 Prioritize Protecting People-based Attacks
The Ninth Annual Cost of Cybercrime Study from Accenture and Ponemon Institute also states, “Countering internal threats is still one of the biggest challenges with a rise in phishing and ransomware attacks, as well as malicious insiders. Cyber criminals are adapting their attack methods. They are targeting the human layer – the weakest link in cyber defense – through increased ransomware and phishing and social engineering attacks as a path to entry.” (19)
4.4 Target Technologies that Reduce Rising Cyber Incident and Breach Costs
Accenture and Ponemon Institute’s Ninth Annual Cost of Cybercrime Study 2019 outlines, “Use automation, advanced analytics and security intelligence to manage the rising cost of discovering attacks, which is the largest component of spending.
By prioritizing technologies that improve Cybersecurity protection, organizations can reduce the consequences of cybercrime and unlock future economic value as higher levels of trust encourage more business from customers.” (19)
Look for Vendors that are NIST-Compliant
Dig Deep to Understand Offerings Before Choosing a Cybersecurity Partner
- Depth of Offering
- Industry Knowledge & Years in Business
- Technology Base & Staying Current with Regulations
- True Functionality and Features that don’t just put up Flags or have End Users Fix Issues but that Automate and Proactively Address Incidents as they Happen as well as manage single event or mass Remediation
Ability to fully Identify, Protect, Detect, Respond and Recover Cyber incidents leveraging the NIST Framework
4.5 Cybersecurity Vendor Checklist
- Years of experience in Cybersecurity
- Understanding of cyber regulations in Financial Services
- Use of best-of-breed software
- Support for Windows and MacOS desktops, laptops, servers and virtual servers
- Support for Android and iOS smartphones and tablets
- Support for BYOD (Bring Your Own Device)
- Offering aligned with the NIST Framework (Identify, Protect, Detect, Respond, Recover)
- WISP setting(s) enforcement without user involvement
- Capacity to stop users from making changes to WISP settings
- Installation, management and update of Cyber tools without user involvement
- Remote mass vulnerability OS update (zero-day) without user involvement
- NIST-based Asset Inventory Report
- 24/7 Cyber monitoring detection and response
- Incident Response expertise and track record
5. Summary
Financial Services Cybersecurity policies, regulations and compliance will continue to evolve over time with new threats and technology advancements. The proof is strong for having a common language like NIST that provides a framework, or standards, to guide companies, vendors and policy makers in creating a secure cyber environment across the industry. Nuances between vendors may exist which is why it’s critical to fully understand differences between offerings based on your environment’s requirements that are ultimately driven by newly formed regulations.
Being secure and having the ability to prove compliance is no longer an option for the often-targeted Financial Services Industry. Creating a cyber team, having proof of compliance, partnering with the right vendors to support you with incidents and breaches, giving employees proper education, protecting remote offices and putting the right boarding and offboarding policies in place for all types of devices are all part of thinking through a comprehensive Cybersecurity Written Information Security Policy (WISP).
Stay Safe!
6. Sources
- ID Theft Center.org – 2018 https://www.idtheftcenter.org/wp-content/uploads/2019/02/ITRC_Generali_The-Impact-of-Cybersecurity-Incidents-on-Financial-Institutions-2018.pdf
- 2015 Morrison & Foerster LLP | mofo.com, Client Alert – February 5, 2015 https://media2.mofo.com/documents/150205seccybersecuritysweep.pdf
- 2018 13th Annual “Cost of a Data Breach Study” by IBM / independently conducted by Ponemon – 2018 https://www.ibm.com/security/data-breach
- Banking Exchange, Article: “Meeting the Threat in 2019: Cybersecurity for Financial Services” – February 11, 2019 https://www.bankingexchange.com/news-feed/item/7770-meeting-the-threat-in-2019-cybersecurity-for-financial-services
- SEC OCIE Cybersecurity Examination Sweep – February 3, 2015 https://www.sec.gov/about/offices/ocie/cybersecurity-examination-sweep-summary.pdf
- Morrison Foerster Discuss SEC Report on Broker Dealer and Investment Adviser Cybersecurity – February 19, 2015 https://clsbluesky.law.columbia.edu/2015/02/19/morrison-foerster-discusses-sec-report-on-broker-dealer-and-investment-adviser-cybersecurity/
- SEC to Launch a Third Cybersecurity Sweep – March 29, 2019 https://www.align.com/blog/sec-ocie-to-launch-a-third-cybersecurity-sweep
- NIST Cyber Framework – History and Creation of Framework – Current https://www.nist.gov/cyberframework/online-learning/history-and-creation-framework
- The Financial Services Sector Cybersecurity Profile (Profile), v1.0 – An Overview and User Guide – Published – October 25, 2018 https://www.fsscc.org/files/galleries/Financial_Services_Sector_Cybersecurity_Profile_Overview_and_User_Guide_2018-10-25.pdf
- Financial Services Sector Unveils NIST Framework-Based Cybersecurity Profile – February 14, 2019 https://create.org/news/financial-services-sector-unveils-nist-framework-based-cybersecurity-profile/
- NIST Financial Services CFS – May 18, 2018 https://www.nist.gov/sites/default/files/documents/2017/05/18/financial_services_csf.pdf
- IAPP – Article FINRA, SEC Provide Broker-Dealers with Motivation, Tools To Get the Job Done – March 24, 2015 https://iapp.org/news/a/finra-sec-provide-broker-dealers-with-motivation-tools-to-get-the-job-done/
- SEC 2018 Press Release – December 20, 2018 https://www.sec.gov/news/press-release/2018-299
- FINRA Rules and Guidance – Current https://www.finra.org/industry/rules-and-guidance
- Risk Insight, Wavestone NIST FSSCC Team Up – February 8, 2018 https://www.riskinsight-wavestone.com/en/2018/08/nist-fsscc-team-up/
- FFIEC Cyber Assessment Tool https://www.ffiec.gov/cyberassessmenttool.htm
- Deloitte Insights, Article: “Pursuing cybersecurity maturity at financial institutions – Survey spotlights key traits among more advanced risk managers” – May 01, 2019 https://www2.deloitte.com/insights/us/en/industry/financial-services/cybersecurity-maturity-financial-institutions-cyber-risk.html
- National Institute of Standards and Technology (NIST), “Framework for improving critical infrastructure cybersecurity,” April 16, 2018. https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
- Ninth Annual Cost of Cybercrime Study, Accenture and Ponemon Institute – March 6, 2019 https://www.accenture.com/us-en/insights/security/cost-cybercrime-study
- Additional Reference Sources
- Allied Market Research – Cyber Security Market Outlook – 2025 – March 2019 https://www.alliedmarketresearch.com/cyber-security-market
- BPI (Bank Policy Institute) ndustry Unveils Cybersecurity Profile to Help Financial Institutions Develop and Maintain Cyber Risk Management Programs – October 25, 2018 https://bpi.com/recent-activity/industry-unveils-cybersecurity-profile-to-help-financial-institutions-develop-and-maintain-cyber-risk-management-programs/


