IDENTIFY
Security Assessment Evidencing & Scanning
When it's time to assess your cyber safeguards, having the right partner with long-standing experience with regulators and authorities reduces your cyber risk and liability.
Security assessments for domains, clouds, systems, networks, and endpoints
With detailed reporting and remediation recommendations
LOWERING BREACH RISK
Cyber Safeguard Evidencing
FCI performs attended sessions with Network and Systems Administrators to review security configuration and validate compliance.
Networks
- Firewall Configuration Evidencing
- Wireless Access Point Configuration Evidencing
Systems
- Microsoft 365 Email Configuration Evidencing
- Active Directory Server Configuration Evidencing
Process
- Attended Sessions with Network and Systems Administrators
- Configuration Review
- Screenshots to Evidence Compliance
- Hardening and Remediation Recommendations
- Evidencing Report
INCREASING COMPLIANCE
Cyber Safeguard Scanning

FCI performs attended sessions with Network and Systems Administrators to review security configuration and validate compliance.
Public
- Network (WAN) Penetration Testing & Vulnerability Scanning
-
Asset Attack Surface & Dark Web Credentials Scanning
(Analysis of Internet-facing domain assets) - Dark Web Credentials Scanning
Private
- Endpoint Vulnerability Scanning
- Network (LAN) Discovery Scanning
- Active Directory Scanning
Process
- Automated Scans & Analysis
- Hardening and Remediation Recommendations
- Evidencing Report
Testimonial
“FCI reduces our liability risk with a thorough Security Assessment of the Firms we acquire.”
Liz Tluchowski
Chief Information and Security Officer Principal

World Insurance Associates LLC
How cybersecurity impacts company valuation in M&A transactions
Are you buying firms or selling yours?
Get an FCI Evidencing & Scanning performed to reduce liabilities
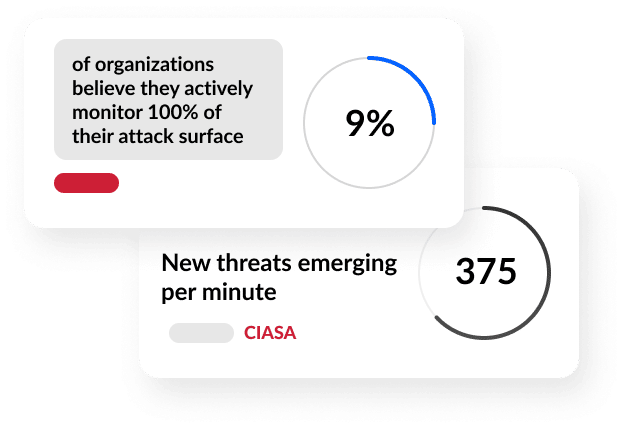
do you know what hackers can see?

Corporate Internet Attack Surface Assessment (CIASA)
Extend your business’s attack surface from internal networks to the farthest reaches of the internet, where attackers have full visibility.